OpenHarmony定制系统签名
| 阿里云国内75折 回扣 微信号:monov8 |
| 阿里云国际,腾讯云国际,低至75折。AWS 93折 免费开户实名账号 代冲值 优惠多多 微信号:monov8 飞机:@monov6 |
参考资料: OpenHarmony应用签名 - 厂商私有签名 OpenHarmony应用签名 - 系统应用签名 OpenHarmony应用签名 - 厂商私有签名的配置和使用 Hap包签名工具 DevEco Studio使用指南(HarmonyOS)应用/服务发布
开发环境
开发平台:Win10 开发板:RK3568 系统版本:OpenHarmony 3.2 Release DevEco Studio 版本:3.1.0.200 full SDK 版本:3.2.11.9
签名简介
为了保证OpenHarmony应用的完整性和来源可靠,在应用构建时需要对应用进行签名。经过签名的应用才能在真机设备上安装、运行、和调试。developtools_hapsigner仓提供了签名工具的源码,包含密钥对生成、CSR文件生成、证书生成、Profile文件签名、Hap包签名等功能。
OpenHarmony系统中有一套默认签名信息,用于应用的开发和调试。当系统厂商正式发布系统时,需要新增或替换私有签名信息,本篇文档将介绍如何生成私有签名并在系统中进行配置。本文档需准备Java和Gradle编译环境。
概念说明
- 非对称密钥对:数据签名/验签的基础,应用签名工具实现了标准的非对称密钥对生成功能(支持的密钥对类型包括ECC P384/256、RSA2048/3072/4096)
- CSR:Certificate Signing Request 证书签发请求是生成证书的前提,他包括证书的公钥、证书主题和私钥签名,在申请证书之前,需要先基于密钥对生成CSR,然后提交给CA签发证书。
- 证书:OpenHarmony采用RFC5280标准构建X509证书信任体系。用于应用签名的OpenHarmony证书共有三级,分为:根CA证书、中间CA证书、最终实体证书,其中最终实体证书分为应用签名证书和profile签名证书。应用签名证书表示应用开发者的身份,可保证系统上安装的应用来源可追溯,profile签名证书实现对profile文件的签名进行验签,保证profile文件的完整性。
- HAP:OpenHarmony Ability Package 是Ability的部署包,OpenHarmony应用代码围绕Ability组件展开,它是由一个或者多个Ability组成。
- Profile文件:HarmonyAppProvision 配置文件,hap包中的描述文件,该描述文件描述了已授权的证书权限和设备ID信息等信息。
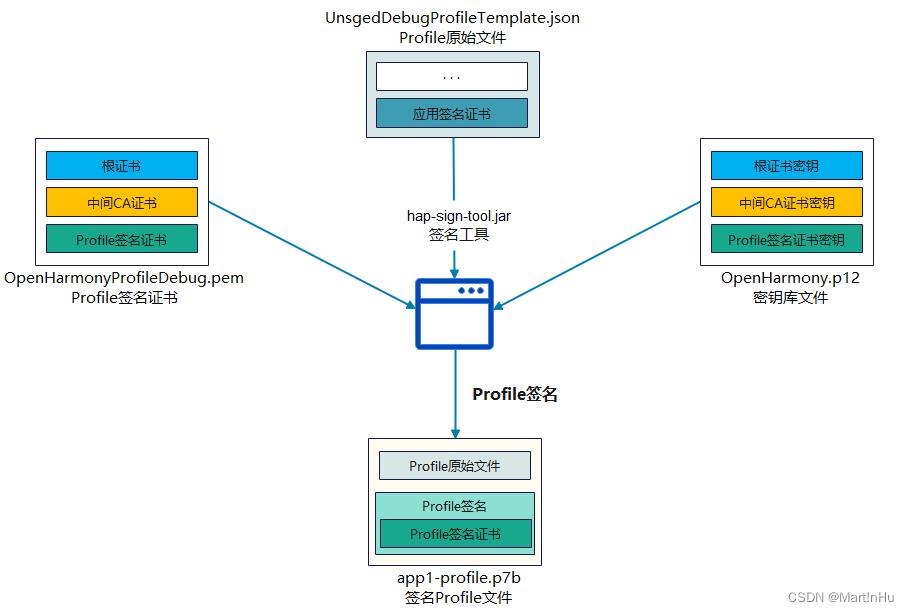
开发者通过IDE进行应用签名时,可在SDK中会获得如下签名相关文件:
签名密钥库文件:OpenHarmony.p12
Profile签名证书:OpenHarmonyProfileRelease.pem、OpenHarmonyProfileDebug.pem
Profile模板文件:UnsgnedReleasedProfileTemplate.json、UnsgnedDebugProfileTemplate.json
签名工具:hap-sign-tool.jar上述文件的使用场景如下图所示。
Profile签名场景:
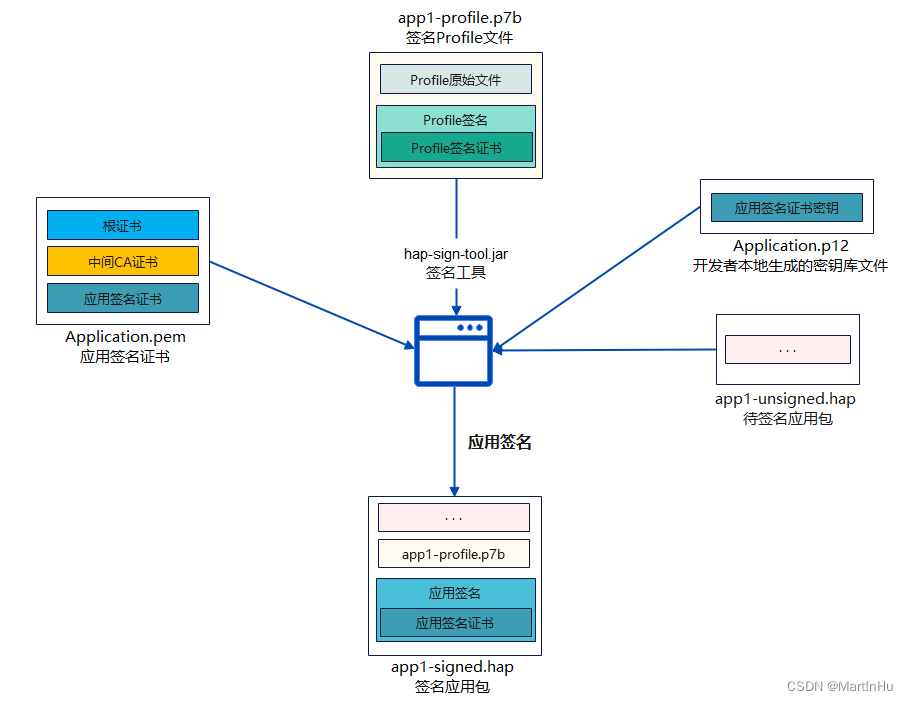
应用签名场景:
准备工作
- Hap签名工具源码:developtools\hapsigner
- 待签名hap包:entry-default-unsigned.hap
- Profile模板文件:Sdk\9\toolchains\lib\UnsgnedReleasedProfileTemplate.json
Hap包签名工具
Hap包签名工具基于Java语言开发,需要在Java8以上Java环境运行 (附:一键签名等脚本文件基于Python语言开发,使用需配置环境python3.x)。签名工具位于源码路径:developtools\hapsigner
developtools\hapsigner
├── autosign # 一键签名脚本
├── dist # SDK预置文件
├── hapsigntool # 主代码
├──hap_sign_tool # 主程序入口,完成输入参数的基础校验
├──hap_sign_tool_lib # 签名工具库,解析命令字和参数列表,实现各模块逻辑功能
├── tools # 自动化测试脚本仓库地址:https://gitee.com/openharmony/developtools_hapsigner.git
编译构建
#进入签名工具所在路径
$ cd developtools/hapsigner/hapsigntool/
#签名工具基于Gradle 7.1编译构建,确认环境已安装配置Gradle环境,并且版本正确
$ gradle -v
Gradle 7.1
#执行gradle build 或者 gradle jar命令编译打包
$ gradle build
BUILD SUCCESSFUL in 22s
14 actionable tasks: 14 executed
#编译完成后得到:developtools\hapsigner\hapsigntool\hap_sign_tool\build\libs\hap-sign-tool.jarhap-sign-tool.jar接口说明
- 生成密钥对
generate-keypair : 生成密钥对
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -keyAlg # 密钥算法,必填项,包括RSA/ECC
├── -keySize # 密钥长度,必填项,RSA算法的长度为2048/3072/4096,ECC算法的长度NIST-P-256/NIST-P-384
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项- 生成证书签名请求
generate-csr : 生成证书签名请求
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -subject # 证书主题,必填项
├── -signAlg # 签名算法,必填项,包括SHA256withRSA / SHA384withRSA / SHA256withECDSA / SHA384withECDSA
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出文件,可选项,如果不填,则直接输出到控制台- 生成根CA/中间CA证书
generate-ca : 生成根CA/中间CA证书,如果密钥不存在,一起生成密钥
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -keyAlg # 密钥算法,必填项,包括RSA/ECC
├── -keySize # 密钥长度,必填项,RSA算法的长度为2048/3072/4096,ECC算法的长度NIST-P-256/NIST-P-384
├── -issuer # 颁发者的主题,可选项,如果不填,表示根CA
├── -issuerKeyAlias # 颁发者的密钥别名,可选项,如果不填,表示根CA
├── -issuerKeyPwd # 颁发者的密钥口令,可选项
├── -subject # 证书主题,必填项
├── -validity # 证书有效期,可选项,默认为3650天
├── -signAlg # 签名算法,必填项,包括SHA256withRSA / SHA384withRSA / SHA256withECDSA / SHA384withECDSA
├── -basicConstraintsPathLen # 路径长度,可选项,默认为0
├── -issuerKeystoreFile # 签发者密钥库文件,可选项,JKS或P12格式
├── -issuerKeystorePwd # 签发者密钥库口令,可选项
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出文件,可选项,如果不填,则直接输出到控制台- 生成应用调试/发布证书
generate-app-cert : 生成应用调试/发布证书
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -issuer # 颁发者的主题,必填项
├── -issuerKeyAlias # 颁发者的密钥别名,必填项
├── -issuerKeyPwd # 颁发者的密钥口令,可选项
├── -subject # 证书主题,必填项
├── -validity # 证书有效期,可选项,默认为3650天
├── -signAlg # 签名算法,必填项,包括SHA256withECDSA / SHA384withECDSA;
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -issuerKeystoreFile # 签发者密钥库文件,可选项,JKS或P12格式
├── -issuerKeystorePwd # 签发者密钥库口令,可选项
├── -outForm # 输出证书文件的格式,包括 cert / certChain,可选项,默认为certChain
├── -rootCaCertFile # outForm为certChain时必填,根CA证书文件
├── -subCaCertFile # outForm为certChain时必填,中间CA证书文件
├── -outFile # 输出证书文件(证书或证书链),可选项,如果不填,则直接输出到控制台- 生成profile调试/发布证书
generate-profile-cert : 生成profile调试/发布证书
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -issuer # 颁发者的主题,必填项
├── -issuerKeyAlias # 颁发者的密钥别名,必填项
├── -issuerKeyPwd # 颁发者的密钥口令,可选项
├── -subject # 证书主题,必填项
├── -validity # 证书有效期,可选项,默认为3650天
├── -signAlg # 签名算法,必填项,包括SHA256withECDSA / SHA384withECDSA;
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -issuerKeystoreFile # 签发者密钥库文件,可选项,JKS或P12格式
├── -issuerKeystorePwd # 签发者密钥库口令,可选项
├── -outForm # 输出证书文件的格式,包括 cert / certChain,可选项,默认为certChain
├── -rootCaCertFile # outForm为certChain时必填,根CA证书文件
├── -subCaCertFile # outForm为certChain时必填,中间CA证书文件
├── -outFile # 输出证书文件(证书或证书链),可选项,如果不填,则直接输出到控制台- 通用证书生成,可以生成自定义证书
generate-cert : 通用证书生成,可以生成自定义证书
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -issuer # 颁发者的主题,必填项
├── -issuerKeyAlias # 颁发者的密钥别名,必填项
├── -issuerKeyPwd # 颁发者的密钥口令,可选项
├── -subject # 证书主题,必填项
├── -validity # 证书有效期,可选项,默认为1095天
├── -keyUsage # 密钥用法,必选项,包括digitalSignature, nonRepudiation, keyEncipherment,
├ dataEncipherment, keyAgreement, certificateSignature, crlSignature,
├ encipherOnly和decipherOnly,如果证书包括多个密钥用法,用逗号分隔
├── -keyUsageCritical # keyUsage是否为关键项,可选项,默认为是
├── -extKeyUsage # 扩展密钥用法,可选项,包括clientAuthentication,serverAuthentication,
├ codeSignature,emailProtection,smartCardLogin,timestamp,ocspSignature
├── -extKeyUsageCritical # extKeyUsage是否为关键项,可选项,默认为否
├── -signAlg # 签名算法,必填项,包括SHA256withRSA/SHA384withRSA/SHA256withECDSA/SHA384withECDSA
├── -basicConstraints # 是否包含basicConstraints,可选项,默认为否
├── -basicConstraintsCritical # basicConstraints是否包含为关键项,可选项,默认为否
├── -basicConstraintsCa # 是否为CA,可选项,默认为否
├── -basicConstraintsPathLen # 路径长度,可选项,默认为0
├── -issuerKeystoreFile # 签发者密钥库文件,可选项,JKS或P12格式
├── -issuerKeystorePwd # 签发者密钥库口令,可选项
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出证书文件,可选项,如果不填,则直接输出到控制台- ProvisionProfile文件签名
sign-profile : ProvisionProfile文件签名
├── -mode # 签名模式,必填项,包括localSign,remoteSign
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -profileCertFile # Profile签名证书(证书链,顺序为最终实体证书-中间CA证书-根证书),必填项
├── -inFile # 输入的原始Provision Profile文件,必填项
├── -signAlg # 签名算法,必填项,包括SHA256withECDSA / SHA384withECDSA
├── -keystoreFile # 密钥库文件,localSign模式时为必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出签名后的Provision Profile文件,p7b格式,必填项- hap应用包签名
sign-app : hap应用包签名
├── -mode # 签名模式,必填项,包括localSign,remoteSign,remoteResign
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -appCertFile # 应用签名证书文件(证书链,顺序为最终实体证书-中间CA证书-根证书),必填项
├── -profileFile # 签名后的Provision Profile文件名,profileSigned为1时为p7b格式,profileSigned为0时为json格式,必填项
├── -profileSigned # 指示profile文件是否带有签名,1表示有签名,0表示没有签名,默认为1。可选项
├── -inForm # 输入的原始文件的格式,zip格式或bin格式,默认zip格式,可选项
├── -inFile # 输入的原始APP包文件,zip格式或bin格式,必填项
├── -signAlg # 签名算法,必填项,包括SHA256withECDSA / SHA384withECDSA
├── -keystoreFile # 密钥库文件,localSign模式时为必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出签名后的包文件,必填项- ProvisionProfile文件验签
verify-profile : ProvisionProfile文件验签
├── -inFile # 已签名的Provision Profile文件,p7b格式,必填项
├── -outFile # 验证结果文件(包含验证结果和profile内容),json格式,可选项;如果不填,则直接输出到控制台- hap应用包文件验签
verify-app : hap应用包文件**验签**
├── -inFile # 已签名的应用包文件,zip格式或bin格式,必填项
├── -outCertChain # 签名的证书链文件,必填项
├── -outProfile # 应用包中的profile文件,必填项命令行签名,生成签名文件
注意:为了方便后续将签名配置导入IDE,在设置密码时需遵守IDE密码规范:
密码必须至少包含8个字符,并包括以下任何两项:
1.小写字母:a-z
2.大写字母: A-Z
3.数字: 0-9
4.特殊字符: `~!@#$%^&*()-_=+\|[{}];:'",<.>/?1、生成密钥对(xxx.p12),keystorePwd为密钥库口令
generate-keypair : 生成密钥对
├── -keyAlias # 密钥别名,【OpenHarmony-ABC】
├── -keyPwd # 密钥口令,【keypair123】
├── -keyAlg # 密钥算法,【ECC】
├── -keySize # 密钥长度,【NIST-P-256】
├── -keystoreFile # 密钥库文件,【OpenHarmony-ABC.p12】
├── -keystorePwd # 密钥库口令,【keystore123】
$ java -jar hap-sign-tool.jar generate-keypair -keyAlias "OpenHarmony-ABC" -keyPwd "keypair123" -keyAlg "ECC" -keySize "NIST-P-256" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123"
#运行成功结果如下
INFO - Start generate-keypair
INFO - generate-keypair success2、生成RootCA证书,subject为RootCA的证书主题,用于配置trusted_root_ca.json。
generate-ca : 生成根CA证书,如果密钥不存在,一起生成密钥
├── -keyAlias # 密钥别名,【OpenHarmony-ABC-rootCA】
├── -keyPwd # 密钥口令,【rootCA123】
├── -keyAlg # 密钥算法,【ECC】
├── -keySize # 密钥长度,【NIST-P-256】
├── -subject # 证书主题,【C=CN, O=OpenHarmony-ABC-rootCA, OU=OpenHarmony-ABC-rootCA Community, CN=OpenHarmony Application Root CA】
├── -validity # 证书有效期,【365】(1年)
├── -signAlg # 签名算法,【SHA256withECDSA】
├── -keystoreFile # 密钥库文件,【./result/OpenHarmony-ABC.p12】
├── -keystorePwd # 密钥库口令,【keystore123】
├── -outFile # 输出文件,【./result/OpenHarmony-ABC-rootCA.cer】
$ java -jar hap-sign-tool.jar generate-ca -keyAlias "OpenHarmony-ABC-rootCA" -keyPwd "rootCA123" -keyAlg "ECC" -keySize "NIST-P-256" -subject "C=CN, O=OpenHarmony-ABC-rootCA, OU=OpenHarmony-ABC-rootCA Community, CN=OpenHarmony Application Root CA" -validity "365" -signAlg "SHA256withECDSA" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -outFile "./result/OpenHarmony-ABC-rootCA.cer"
#运行成功结果如下
INFO - Start generate-ca
INFO - ./result/OpenHarmony-ABC.p12 is exist. Try to load it with given passwd
INFO - generate-ca success3、生成SubCA证书
generate-ca : 生成根CA证书,如果密钥不存在,一起生成密钥
├── -keyAlias # 密钥别名,【OpenHarmony-ABC-subCA】
├── -keyPwd # 密钥口令,【subCA123】
├── -keyAlg # 密钥算法,【ECC】
├── -keySize # 密钥长度,【NIST-P-256】
├── -issuer # 颁发者的主题,【C=CN, O=OpenHarmony-ABC-rootCA, OU=OpenHarmony-ABC-rootCA Community, CN=OpenHarmony Application Root CA】
├── -issuerKeyAlias # 颁发者的密钥别名,【OpenHarmony-ABC-rootCA】
├── -issuerKeyPwd # 颁发者的密钥口令,【rootCA123】
├── -subject # 证书主题,【C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application Sub CA】
├── -validity # 证书有效期,【365】(1年)
├── -signAlg # 签名算法,【SHA256withECDSA】
├── -keystoreFile # 密钥库文件,【./result/OpenHarmony-ABC.p12】
├── -keystorePwd # 密钥库口令,【keystore123】
├── -outFile # 输出文件,【./result/OpenHarmony-ABC-subCA.cer】
$ java -jar hap-sign-tool.jar generate-ca -keyAlias "OpenHarmony-ABC-subCA" -keyPwd "subCA123" -keyAlg "ECC" -keySize "NIST-P-256" -issuer "C=CN, O=OpenHarmony-ABC-rootCA, OU=OpenHarmony-ABC-rootCA Community, CN=OpenHarmony Application Root CA" -issuerKeyAlias "OpenHarmony-ABC-rootCA" -issuerKeyPwd "rootCA123" -subject "C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application Sub CA" -validity "365" -signAlg "SHA256withECDSA" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -outFile "./result/OpenHarmony-ABC-subCA.cer"
#运行成功结果如下
INFO - Start generate-ca
INFO - ./result/OpenHarmony-ABC.p12 is exist. Try to load it with given passwd
INFO - generate-ca success4、生成应用调试/发布证书,subject用于配置trusted_apps_sources.json中的app-signing-cert项。
generate-app-cert : 生成应用调试/发布证书
├── -keyAlias # 密钥别名,【OpenHarmony-ABC-subCA】
├── -keyPwd # 密钥口令,【subCA123】
├── -issuer # 颁发者的主题,【C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application Sub CA" -issuerKeyAlias "OpenHarmony-ABC-subCA】
├── -issuerKeyAlias # 颁发者的密钥别名,【OpenHarmony-ABC-subCA】
├── -issuerKeyPwd # 颁发者的密钥口令,【subCA123】
├── -subject # 证书主题,【C=CN, O=OpenHarmony-ABC-app-cert, OU=OpenHarmony-ABC-app-cert Community, CN=OpenHarmony Application Release】
├── -validity # 证书有效期,【365】
├── -signAlg # 签名算法,【SHA256withECDSA】
├── -keystoreFile # 密钥库文件,【./result/OpenHarmony-ABC.p12】
├── -keystorePwd # 密钥库口令,【keystore123】
├── -rootCaCertFile # outForm为certChain时必填,根CA证书文件【./result/OpenHarmony-ABC-rootCA.cer】
├── -subCaCertFile # outForm为certChain时必填,中间CA证书文件【./result/OpenHarmony-ABC-subCA.cer】
├── -outFile # 输出证书文件(证书或证书链),【./result/OpenHarmony-ABC-app-cert.pem】
$ java -jar hap-sign-tool.jar generate-app-cert -keyAlias "OpenHarmony-ABC-subCA" -keyPwd "subCA123" -issuer "C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application Sub CA" -issuerKeyAlias "OpenHarmony-ABC-subCA" -issuerKeyPwd "subCA123" -subject "C=CN, O=OpenHarmony-ABC-app-cert, OU=OpenHarmony-ABC-app-cert Community, CN=OpenHarmony Application Release" -validity "365" -signAlg "SHA256withECDSA" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -rootCaCertFile "./result/OpenHarmony-ABC-rootCA.cer" -outForm "certChain" -subCaCertFile "./result/OpenHarmony-ABC-subCA.cer" -outFile "./result/OpenHarmony-ABC-app-cert.pem"
#运行成功结果如下
INFO - Start generate-app-cert
INFO - ./result/OpenHarmony-ABC.p12 is exist. Try to load it with given passwd
INFO - generate-app-cert success5、生成ProfileCA证书,subject用于配置trusted_apps_sources.json中的issuer-ca项
generate-ca : 生成ProfileCA证书,如果密钥不存在,一起生成密钥
├── -keyAlias # 密钥别名,【OpenHarmony-ABC-profileCA】
├── -keyPwd # 密钥口令,【profileCA123】
├── -keyAlg # 密钥算法,【ECC】
├── -keySize # 密钥长度,【NIST-P-256】
├── -issuer # 颁发者的主题,【C=CN, O=OpenHarmony-ABC-rootCA, OU=OpenHarmony-ABC-rootCA Community, CN=OpenHarmony Application Root CA】
├── -issuerKeyAlias # 颁发者的密钥别名,【OpenHarmony-ABC-rootCA】
├── -issuerKeyPwd # 颁发者的密钥口令,【rootCA123】
├── -subject # 证书主题,【C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application Sub CA】
├── -validity # 证书有效期,【365】(1年)
├── -signAlg # 签名算法,【SHA256withECDSA】
├── -keystoreFile # 密钥库文件,【./result/OpenHarmony-ABC.p12】
├── -keystorePwd # 密钥库口令,【keystore123】
├── -outFile # 输出文件,【./result/OpenHarmony-ABC-profileCA.cer】
$ java -jar hap-sign-tool.jar generate-ca -keyAlias "OpenHarmony-ABC-profileCA" -keyPwd "profileCA123" -keyAlg "ECC" -keySize "NIST-P-256" -issuer "C=CN, O=OpenHarmony-ABC-rootCA, OU=OpenHarmony-ABC-rootCA Community, CN=OpenHarmony Application Root CA" -issuerKeyAlias "OpenHarmony-ABC-rootCA" -issuerKeyPwd "rootCA123" -subject "C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application CA" -validity "365" -signAlg "SHA256withECDSA" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -outFile "./result/OpenHarmony-ABC-profileCA.cer"
#运行成功结果如下
INFO - Start generate-ca
INFO - ./result/OpenHarmony-ABC.p12 is exist. Try to load it with given passwd
INFO - generate-ca success6、生成应用Release版profile调试/发布证书,subject用于配置trusted_apps_sources.json中的profile-signing-certificate项。
generate-profile-cert : 生成Release版本profile调试/发布证书
├── -keyAlias # 密钥别名,【OpenHarmony-ABC-profileCA】
├── -keyPwd # 密钥口令,【profileCA123】
├── -issuer # 颁发者的主题,【C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application CA】
├── -issuerKeyAlias # 颁发者的密钥别名,【OpenHarmony-ABC-profileCA】
├── -issuerKeyPwd # 颁发者的密钥口令,【profileCA123】
├── -subject # 证书主题,【C=CN, O=OpenHarmony-ABC-profile-cert, OU=OpenHarmony-ABC-profile-cert Community, CN=OpenHarmony Application Profile Release】
├── -validity # 证书有效期,【365】
├── -signAlg # 签名算法,【SHA256withECDSA】
├── -keystoreFile # 密钥库文件,【./result/OpenHarmony-ABC.p12】
├── -keystorePwd # 密钥库口令,【keystore123】
├── -outForm # 输出证书文件的格式,包括 cert / certChain,【certChain】
├── -rootCaCertFile # outForm为certChain时必填,根CA证书文件【./result/OpenHarmony-ABC-rootCA.cer】
├── -subCaCertFile # outForm为certChain时必填,中间CA证书文件【./result/OpenHarmony-ABC-profileCA.cer】
├── -outFile # 输出证书文件(证书或证书链),【./result/OpenHarmony-ABC-profile-cert-release.pem】
$ java -jar hap-sign-tool.jar generate-profile-cert -keyAlias "OpenHarmony-ABC-profileCA" -keyPwd "profileCA123" -issuer "C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application CA" -issuerKeyAlias "OpenHarmony-ABC-profileCA" -issuerKeyPwd "profileCA123" -subject "C=CN, O=OpenHarmony-ABC-profile-cert, OU=OpenHarmony-ABC-profile-cert Community, CN=OpenHarmony Application Profile Release" -validity "365" -signAlg "SHA256withECDSA" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -outForm "certChain" -rootCaCertFile "./result/OpenHarmony-ABC-rootCA.cer" -subCaCertFile "./result/OpenHarmony-ABC-profileCA.cer" -outFile "./result/OpenHarmony-ABC-profile-cert-release.pem"
#运行成功结果如下
INFO - Start generate-profile-cert
INFO - ./result/OpenHarmony-ABC.p12 is exist. Try to load it with given passwd
INFO - generate-profile-cert success7、生成应用Debug版profile调试/发布证书,subject用于配置trusted_apps_sources.json中的profile-debug-signing-certificate项
generate-profile-cert : 生成Debug版本profile调试/发布证书
├── -keyAlias # 密钥别名,【OpenHarmony-ABC-profileCA】
├── -keyPwd # 密钥口令,【profileCA123】
├── -issuer # 颁发者的主题,【C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application CA】
├── -issuerKeyAlias # 颁发者的密钥别名,【OpenHarmony-ABC-profileCA】
├── -issuerKeyPwd # 颁发者的密钥口令,【profileCA123】
├── -subject # 证书主题,【C=CN, O=OpenHarmony-ABC-profile-cert, OU=OpenHarmony-ABC-profile-cert Community, CN=OpenHarmony Application Profile Debug】
├── -validity # 证书有效期,【365】
├── -signAlg # 签名算法,【SHA256withECDSA】
├── -keystoreFile # 密钥库文件,【./result/OpenHarmony-ABC.p12】
├── -keystorePwd # 密钥库口令,【keystore123】
├── -outForm # 输出证书文件的格式,包括 cert / certChain,【certChain】
├── -rootCaCertFile # outForm为certChain时必填,根CA证书文件【./result/OpenHarmony-ABC-rootCA.cer】
├── -subCaCertFile # outForm为certChain时必填,中间CA证书文件【./result/OpenHarmony-ABC-profileCA.cer】
├── -outFile # 输出证书文件(证书或证书链),【./result/OpenHarmony-ABC-profile-cert-debug.pem】
$ java -jar hap-sign-tool.jar generate-profile-cert -keyAlias "OpenHarmony-ABC-profileCA" -keyPwd "profileCA123" -issuer "C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application CA" -issuerKeyAlias "OpenHarmony-ABC-profileCA" -issuerKeyPwd "profileCA123" -subject "C=CN, O=OpenHarmony-ABC-profile-cert, OU=OpenHarmony-ABC-profile-cert Community, CN=OpenHarmony Application Profile Debug" -validity "365" -signAlg "SHA256withECDSA" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -outForm "certChain" -rootCaCertFile "./result/OpenHarmony-ABC-rootCA.cer" -subCaCertFile "./result/OpenHarmony-ABC-profileCA.cer" -outFile "./result/OpenHarmony-ABC-profile-cert-debug.pem"
#运行成功结果如下
INFO - Start generate-profile-cert
INFO - ./result/OpenHarmony-ABC.p12 is exist. Try to load it with given passwd
INFO - generate-profile-cert success经过以上步骤得到签名文件如下:
$ ls -al result/
OpenHarmony-ABC-app-cert.pem
OpenHarmony-ABC.p12
OpenHarmony-ABC-profileCA.cer
OpenHarmony-ABC-profile-cert-debug.pem
OpenHarmony-ABC-profile-cert-release.pem
OpenHarmony-ABC-rootCA.cer
OpenHarmony-ABC-subCA.cer8、将OpenHarmony-ABC-app-cert.pem中第一部分的密钥,把回车转换为\n字符,放入UnsgnedReleasedProfileTemplate.json的distribution-certificate中
-----BEGIN CERTIFICATE-----
MIICZjCCAgygAwIBAgIEXPrigDAKBggqhkjOPQQDAjCBgDELMAkGA1UEBhMCQ04x
HjAcBgNVBAoMFU9wZW5IYXJtb255LUFCQy1zdWJDQTEoMCYGA1UECwwfT3Blbkhh
cm1vbnktQUJDLXN1YkNBIENvbW11bml0eTEnMCUGA1UEAwweT3Blbkhhcm1vbnkg
QXBwbGljYXRpb24gU3ViIENBMB4XDTIzMDYyODA1MjgwMloXDTI0MDYyNzA1Mjgw
MlowgYcxCzAJBgNVBAYTAkNOMSEwHwYDVQQKDBhPcGVuSGFybW9ueS1BQkMtYXBw
LWNlcnQxKzApBgNVBAsMIk9wZW5IYXJtb255LUFCQy1hcHAtY2VydCBDb21tdW5p
dHkxKDAmBgNVBAMMH09wZW5IYXJtb255IEFwcGxpY2F0aW9uIFJlbGVhc2UwWTAT
BgcqhkjOPQIBBggqhkjOPQMBBwNCAARvPLo0HPZroleu81PSWDEmB2cGI+EHUM7b
w95BBsaThBfjbtt37oNICJRGaBWSxmCSxbU557Ci7IRE7o/vJaM0o2swaTAdBgNV
HQ4EFgQUUvatlguoLp2hFrlme6a0KrlNF2AwCQYDVR0TBAIwADAOBgNVHQ8BAf8E
BAMCB4AwEwYDVR0lBAwwCgYIKwYBBQUHAwMwGAYMKwYBBAGPWwKCeAEDBAgwBgIB
AQoBADAKBggqhkjOPQQDAgNIADBFAiAcH26/JhsRiHqDEX7A95Vb2VkIm8xUYJs5
pz2Nzde6yAIhAJrYHxuTVuhdgkJ7IL5WNmU+YwJdp6Li+rIb0JFe2ZmR
-----END CERTIFICATE-----转换后:
-----BEGIN CERTIFICATE-----\nMIICZjCCAgygAwIBAgIEXPrigDAKBggqhkjOPQQDAjCBgDELMAkGA1UEBhMCQ04x\nHjAcBgNVBAoMFU9wZW5IYXJtb255LUFCQy1zdWJDQTEoMCYGA1UECwwfT3Blbkhh\ncm1vbnktQUJDLXN1YkNBIENvbW11bml0eTEnMCUGA1UEAwweT3Blbkhhcm1vbnkg\nQXBwbGljYXRpb24gU3ViIENBMB4XDTIzMDYyODA1MjgwMloXDTI0MDYyNzA1Mjgw\nMlowgYcxCzAJBgNVBAYTAkNOMSEwHwYDVQQKDBhPcGVuSGFybW9ueS1BQkMtYXBw\nLWNlcnQxKzApBgNVBAsMIk9wZW5IYXJtb255LUFCQy1hcHAtY2VydCBDb21tdW5p\ndHkxKDAmBgNVBAMMH09wZW5IYXJtb255IEFwcGxpY2F0aW9uIFJlbGVhc2UwWTAT\nBgcqhkjOPQIBBggqhkjOPQMBBwNCAARvPLo0HPZroleu81PSWDEmB2cGI+EHUM7b\nw95BBsaThBfjbtt37oNICJRGaBWSxmCSxbU557Ci7IRE7o/vJaM0o2swaTAdBgNV\nHQ4EFgQUUvatlguoLp2hFrlme6a0KrlNF2AwCQYDVR0TBAIwADAOBgNVHQ8BAf8E\nBAMCB4AwEwYDVR0lBAwwCgYIKwYBBQUHAwMwGAYMKwYBBAGPWwKCeAEDBAgwBgIB\nAQoBADAKBggqhkjOPQQDAgNIADBFAiAcH26/JhsRiHqDEX7A95Vb2VkIm8xUYJs5\npz2Nzde6yAIhAJrYHxuTVuhdgkJ7IL5WNmU+YwJdp6Li+rIb0JFe2ZmR\n-----END CERTIFICATE-----\n将转换后的密钥写入UnsgnedReleasedProfileTemplate.json的distribution-certificate中注意:bundle-name需与应用包名匹配,否则安装时:error: failed to install bundle. error: verify signature failed.
"bundle-info": {
"developer-id": "OpenHarmony",
"distribution-certificate": "-----BEGIN CERTIFICATE-----\nMIICZjCCAgygAwIBAgIEXPrigDAKBggqhkjOPQQDAjCBgDELMAkGA1UEBhMCQ04x\nHjAcBgNVBAoMFU9wZW5IYXJtb255LUFCQy1zdWJDQTEoMCYGA1UECwwfT3Blbkhh\ncm1vbnktQUJDLXN1YkNBIENvbW11bml0eTEnMCUGA1UEAwweT3Blbkhhcm1vbnkg\nQXBwbGljYXRpb24gU3ViIENBMB4XDTIzMDYyODA1MjgwMloXDTI0MDYyNzA1Mjgw\nMlowgYcxCzAJBgNVBAYTAkNOMSEwHwYDVQQKDBhPcGVuSGFybW9ueS1BQkMtYXBw\nLWNlcnQxKzApBgNVBAsMIk9wZW5IYXJtb255LUFCQy1hcHAtY2VydCBDb21tdW5p\ndHkxKDAmBgNVBAMMH09wZW5IYXJtb255IEFwcGxpY2F0aW9uIFJlbGVhc2UwWTAT\nBgcqhkjOPQIBBggqhkjOPQMBBwNCAARvPLo0HPZroleu81PSWDEmB2cGI+EHUM7b\nw95BBsaThBfjbtt37oNICJRGaBWSxmCSxbU557Ci7IRE7o/vJaM0o2swaTAdBgNV\nHQ4EFgQUUvatlguoLp2hFrlme6a0KrlNF2AwCQYDVR0TBAIwADAOBgNVHQ8BAf8E\nBAMCB4AwEwYDVR0lBAwwCgYIKwYBBQUHAwMwGAYMKwYBBAGPWwKCeAEDBAgwBgIB\nAQoBADAKBggqhkjOPQQDAgNIADBFAiAcH26/JhsRiHqDEX7A95Vb2VkIm8xUYJs5\npz2Nzde6yAIhAJrYHxuTVuhdgkJ7IL5WNmU+YwJdp6Li+rIb0JFe2ZmR\n-----END CERTIFICATE-----\n",
"bundle-name": "com.example.mysigndemo",
"apl": "system_basic",
"app-feature": "hos_system_app"
}9、ProvisionProfile文件签名
sign-profile : ProvisionProfile文件签名
├── -mode # 签名模式,【localSign】
├── -keyAlias # 密钥别名,【OpenHarmony-ABC-profileCA】
├── -keyPwd # 密钥口令,【profileCA123】
├── -profileCertFile # Profile签名证书,【./result/OpenHarmony-ABC-profile-cert-release.pem】
├── -inFile # 输入的原始Provision Profile文件,【UnsgnedReleasedProfileTemplate.json】
├── -signAlg # 签名算法,【SHA256withECDSA】
├── -keystoreFile # 密钥库文件,【./result/OpenHarmony-ABC.p12】
├── -keystorePwd # 密钥库口令,【keystore123】
├── -outFile # 输出签名后的Provision Profile文件,p7b格式,【./result/Openharmony-signtest.p7b】
$ java -jar hap-sign-tool.jar sign-profile -mode "localSign" -keyAlias "OpenHarmony-ABC-profileCA" -keyPwd "profileCA123" -profileCertFile "./result/OpenHarmony-ABC-profile-cert-release.pem" -inFile "UnsgnedReleasedProfileTemplate.json" -signAlg "SHA256withECDSA" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -outFile "./result/Openharmony-signtest.p7b"
#运行成功结果如下
INFO - Start sign-profile
INFO - ./result/OpenHarmony-ABC.p12 is exist. Try to load it with given passwd
INFO - sign-profile success
#ProvisionProfile文件验签
verify-profile : ProvisionProfile文件验签
├── -inFile # 已签名的Provision Profile文件,【】
├── -outFile # 验证结果文件(包含验证结果和profile内容),【】
$ java -jar hap-sign-tool.jar verify-profile -inFile "./result/Openharmony-signtest.p7b" -outFile "./result/Openharmony-verify-profile-result.json"
#运行成功结果如下,详细结果见Openharmony-verify-profile-result.json
INFO - Start verify-profile
INFO - verify-profile success10、hap应用包签名
sign-app : hap应用包签名
├── -mode # 签名模式,【localSign】
├── -keyAlias # 密钥别名,【OpenHarmony-ABC-subCA】
├── -keyPwd # 密钥口令,【subCA123】
├── -appCertFile # 应用签名证书文件(证书链,顺序为最终实体证书-中间CA证书-根证书),【./result/OpenHarmony-ABC-app-cert.pem】
├── -profileFile # 签名后的Provision Profile文件名,profileSigned为1时为p7b格式,profileSigned为0时为json格式,【./result/Openharmony-signtest.p7b】
├── -inFile # 输入的原始APP包文件,【entry-default-unsigned.hap】
├── -signAlg # 签名算法,【SHA256withECDSA】
├── -keystoreFile # 密钥库文件,【OpenHarmony-ABC.p12】
├── -keystorePwd # 密钥库口令,【keystore123】
├── -outFile # 输出签名后的包文件,【./result/entry-default-signed.hap】
$ java -jar hap-sign-tool.jar sign-app -mode "localSign" -keyAlias "OpenHarmony-ABC-subCA" -keyPwd "subCA123" -appCertFile "./result/OpenHarmony-ABC-app-cert.pem" -profileFile "./result/Openharmony-signtest.p7b" -signAlg "SHA256withECDSA" -inFile "entry-default-unsigned.hap" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -outFile "./result/entry-default-signed.hap"
#运行成功结果如下
INFO - Start sign-app
INFO - certificate in profile: OpenHarmony Application Release
INFO - ./result/OpenHarmony-ABC.p12 is exist. Try to load it with given passwd
INFO - Add sign data in sign info list success.
INFO - Generate signing block success, begin write it to output file
INFO - Sign Hap success!
INFO - sign-app success
verify-app : hap应用包文件验签
├── -inFile # 已签名的应用包文件,【./result/entry-default-signed.hap】
├── -outCertChain # 签名的证书链文件,【./result/OpenHarmony-ABC-subCA.cer】
├── -outProfile # 应用包中的profile文件,【Openharmony-signtest.p7b】
$ java -jar hap-sign-tool.jar verify-app -inFile "./result/entry-default-signed.hap" -outCertChain "./result/OpenHarmony-ABC-subCA.cer" -outProfile "Openharmony-signtest.p7b" > ./result/OpenHarmony-verify-app-result.json
#运行成功结果如下,详细结果见OpenHarmony-verify-app-result.json
06-28 16:26:35 WARN - Missing parameter: outproof得到Profile签名文件和已签名的hap
Openharmony-signtest.p7b
entry-default-signed.hap验证定制签名
验证定制签名主要通过
- hdc安装已签名的hap
- IDE导入签名配置,编译安装hap
hdc验证
上述步骤生成的entry-default-signed.hap为定制签名的hap,与系统默认签名配置不同,因此直接安装会失败:
> hdc install xxx\ohos_signtest\result\entry-default-signed.hap
[Info]App install path:ohos_signtest\result\entry-default-signed.hap, queuesize:0, msg:error: failed to install bundle. error: fail to verify pkcs7 file.
AppMod finish因此需要修改默认系统证书配置文件trusted_apps_sources.json和trusted_root_ca.json
设备路径:/etc/security/trusted_apps_sources.json、/etc/security/trusted_root_ca.json
源码路径:base/security/appverify/interfaces/innerkits/appverify/config/OpenHarmony/trusted_apps_sources.json、
base/security/appverify/interfaces/innerkits/appverify/config/OpenHarmony/trusted_root_ca.json
- trusted_apps_sources.json修改如下:
#兼容则新添加一下配置项,强制则替换默认OpenHarmony apps配置
{
"name":"OpenHarmony-ABC apps",
"app-signing-cert":"C=CN, O=OpenHarmony-ABC-app-cert, OU=OpenHarmony-ABC-app-cert Community, CN=OpenHarmony Application Release",
"profile-signing-certificate":"C=CN, O=OpenHarmony-ABC-profile-cert, OU=OpenHarmony-ABC-profile-cert Community, CN=OpenHarmony Application Profile Release",
"profile-debug-signing-certificate":"C=CN, O=OpenHarmony-ABC-profile-cert, OU=OpenHarmony-ABC-profile-cert Community, CN=OpenHarmony Application Profile Debug",
"issuer-ca":"C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application CA",
"max-certs-path":3,
"critialcal-cert-extension":["keyusage"]
}其中
name:授信应用群名称,无特殊要求,可自定义
app-signing-cert:应用签名证书主题,与OpenHarmony-ABC-app-cert.pem subject保持一致
profile-signing-certificate:profile Release签名证书主题,与OpenHarmony-ABC-profile-cert-release.pem subject保持一致
profile-debug-signing-certificate:profile Debug签名证书主题,与OpenHarmony-ABC-profile-cert-debug.pem subject保持一致
issuer-ca:profileCA主题,与OpenHarmony-ABC-profileCA.cer subject保持一致
subject中的C、O、OU、CN含义如下:
C:国家/地区代码,如CN
O:组织名称,如HUAWEI
OU:组织单位名称,如HUAWEI IDE
CN:名字与姓氏,建议与别名一致- 修改trusted_root_ca.json 文件:将 OpenHarmony-ABC-rootCA.cer 密钥信息处理后加入到文件中。
-----BEGIN CERTIFICATE-----
MIICQDCCAeagAwIBAgIFANIukcQwCgYIKoZIzj0EAwIwgYMxCzAJBgNVBAYTAkNO
MR8wHQYDVQQKDBZPcGVuSGFybW9ueS1BQkMtcm9vdENBMSkwJwYDVQQLDCBPcGVu
SGFybW9ueS1BQkMtcm9vdENBIENvbW11bml0eTEoMCYGA1UEAwwfT3Blbkhhcm1v
bnkgQXBwbGljYXRpb24gUm9vdCBDQTAeFw0yMzA2MjgwMzE3NTlaFw0yNDA2Mjcw
MzE3NTlaMIGDMQswCQYDVQQGEwJDTjEfMB0GA1UECgwWT3Blbkhhcm1vbnktQUJD
LXJvb3RDQTEpMCcGA1UECwwgT3Blbkhhcm1vbnktQUJDLXJvb3RDQSBDb21tdW5p
dHkxKDAmBgNVBAMMH09wZW5IYXJtb255IEFwcGxpY2F0aW9uIFJvb3QgQ0EwWTAT
BgcqhkjOPQIBBggqhkjOPQMBBwNCAAQ/IK5FcvYOsKF8OpuiHRcR6zawSiPmVYp2
AKahLN5CxjMTpVj14t23yG8RScJEOjuKUxh8SAqYr7lB0riOWJodo0UwQzAdBgNV
HQ4EFgQUeb2WbI8s7xczwXlsuk8fo9eqmQUwEgYDVR0TAQH/BAgwBgEB/wIBADAO
BgNVHQ8BAf8EBAMCAQYwCgYIKoZIzj0EAwIDSAAwRQIhANv5RhH5UtH0SXOh7k7+
AVcBkn3Dqfdbu/LTShclS+APAiBpEe3s49fxpW7pNbGzdMEgaqXafuf5+YTT5VqF
8PYydA==
-----END CERTIFICATE-----处理后:
-----BEGIN CERTIFICATE-----\nMIICQDCCAeagAwIBAgIFANIukcQwCgYIKoZIzj0EAwIwgYMxCzAJBgNVBAYTAkNO\nMR8wHQYDVQQKDBZPcGVuSGFybW9ueS1BQkMtcm9vdENBMSkwJwYDVQQLDCBPcGVu\nSGFybW9ueS1BQkMtcm9vdENBIENvbW11bml0eTEoMCYGA1UEAwwfT3Blbkhhcm1v\nbnkgQXBwbGljYXRpb24gUm9vdCBDQTAeFw0yMzA2MjgwMzE3NTlaFw0yNDA2Mjcw\nMzE3NTlaMIGDMQswCQYDVQQGEwJDTjEfMB0GA1UECgwWT3Blbkhhcm1vbnktQUJD\nLXJvb3RDQTEpMCcGA1UECwwgT3Blbkhhcm1vbnktQUJDLXJvb3RDQSBDb21tdW5p\ndHkxKDAmBgNVBAMMH09wZW5IYXJtb255IEFwcGxpY2F0aW9uIFJvb3QgQ0EwWTAT\nBgcqhkjOPQIBBggqhkjOPQMBBwNCAAQ/IK5FcvYOsKF8OpuiHRcR6zawSiPmVYp2\nAKahLN5CxjMTpVj14t23yG8RScJEOjuKUxh8SAqYr7lB0riOWJodo0UwQzAdBgNV\nHQ4EFgQUeb2WbI8s7xczwXlsuk8fo9eqmQUwEgYDVR0TAQH/BAgwBgEB/wIBADAO\nBgNVHQ8BAf8EBAMCAQYwCgYIKoZIzj0EAwIDSAAwRQIhANv5RhH5UtH0SXOh7k7+\nAVcBkn3Dqfdbu/LTShclS+APAiBpEe3s49fxpW7pNbGzdMEgaqXafuf5+YTT5VqF\n8PYydA==\n-----END CERTIFICATE-----\n写入trusted_root_ca.json
#兼容则新添加一下配置项,强制则替换默认rootCA配置
{
"C=CN, O=OpenHarmony-ABC-rootCA, OU=OpenHarmony-ABC-rootCA Community, CN=OpenHarmony Application Root CA":"-----BEGIN CERTIFICATE-----\nMIICQDCCAeagAwIBAgIFANIukcQwCgYIKoZIzj0EAwIwgYMxCzAJBgNVBAYTAkNO\nMR8wHQYDVQQKDBZPcGVuSGFybW9ueS1BQkMtcm9vdENBMSkwJwYDVQQLDCBPcGVu\nSGFybW9ueS1BQkMtcm9vdENBIENvbW11bml0eTEoMCYGA1UEAwwfT3Blbkhhcm1v\nbnkgQXBwbGljYXRpb24gUm9vdCBDQTAeFw0yMzA2MjgwMzE3NTlaFw0yNDA2Mjcw\nMzE3NTlaMIGDMQswCQYDVQQGEwJDTjEfMB0GA1UECgwWT3Blbkhhcm1vbnktQUJD\nLXJvb3RDQTEpMCcGA1UECwwgT3Blbkhhcm1vbnktQUJDLXJvb3RDQSBDb21tdW5p\ndHkxKDAmBgNVBAMMH09wZW5IYXJtb255IEFwcGxpY2F0aW9uIFJvb3QgQ0EwWTAT\nBgcqhkjOPQIBBggqhkjOPQMBBwNCAAQ/IK5FcvYOsKF8OpuiHRcR6zawSiPmVYp2\nAKahLN5CxjMTpVj14t23yG8RScJEOjuKUxh8SAqYr7lB0riOWJodo0UwQzAdBgNV\nHQ4EFgQUeb2WbI8s7xczwXlsuk8fo9eqmQUwEgYDVR0TAQH/BAgwBgEB/wIBADAO\nBgNVHQ8BAf8EBAMCAQYwCgYIKoZIzj0EAwIDSAAwRQIhANv5RhH5UtH0SXOh7k7+\nAVcBkn3Dqfdbu/LTShclS+APAiBpEe3s49fxpW7pNbGzdMEgaqXafuf5+YTT5VqF\n8PYydA==\n-----END CERTIFICATE-----\n"
}将更新后的trusted_apps_sources.json和trusted_root_ca.json推送至系统中并重启:
> hdc shell "mount -o remount,rw /"
> hdc file send xxx\test\ohos_signtest\trusted_apps_sources.json /etc/security/trusted_apps_sources.json
FileTransfer finish, Size:2168, File count = 1, time:21ms rate:103.24kB/s
> hdc file send xxx\test\ohos_signtest\trusted_root_ca.json /etc/security/trusted_root_ca.json
FileTransfer finish, Size:1847, File count = 1, time:17ms rate:108.65kB/s
> hdc shell reboot安装签名应用
> hdc install xxx\test\ohos_signtest\demo\entry-default-signed.hap
[Info]App install path:xxx\test\ohos_signtool\demo\entry-default-signed.hap, queuesize:0, msg:install bundle successfully.
AppMod finish5、IDE验证
将生成的定制系统签名配置文件导入IDE,使用定制签名对hap进行签名,编译后直接可安装至设备。打开IDE进行签名配置:
IDE->File->ProjectStructure->Signing Configs
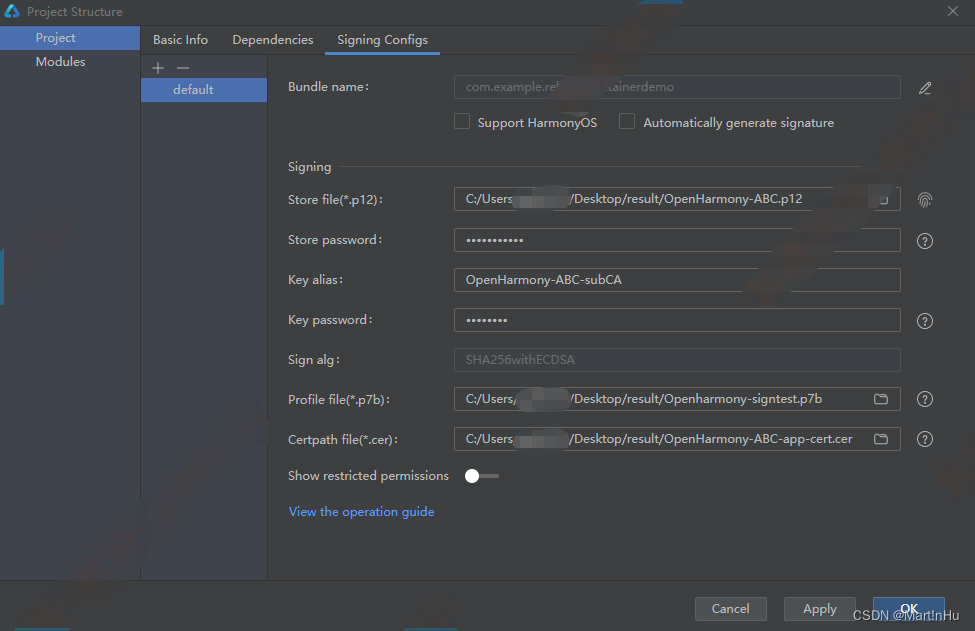
其中:
- Store file(*.p12):密钥库文件,选择OpenHarmony-ABC.p12
- Store password:密钥库密码,keystore123
- Key alias:密钥别名,OpenHarmony-ABC-subCA
- Key password:密钥密码,subCA123
- Sign alg:签名算法,默认为SHA256withECDSA
- Profile file(*.p7b):profile签名文件,选择Openharmony-signtest.p7b
- Certpath file(*.cer):应用调试/发布证书,
将OpenHarmony-ABC-app-cert.pem重命名为OpenHarmony-ABC-app-cert.cer
查看项目build-profile.json5签名配置是否已更新
"signingConfigs": [
{
"name": "default",
"material": {
"storePassword": "0000001BD38A4D685B71DC9660538FE27BFDFFA31735901B6EF4690690D4AF8E91936D04D6571E60B56376",
"certpath": "C:/Users/xxx/Desktop/result/OpenHarmony-ABC-app-cert.cer",
"keyAlias": "OpenHarmony-ABC-subCA",
"keyPassword": "000000183110ABA8E0FE869D85057E2EADA895DDBE7C2CF30A292A217AFA8239B547506E250FD5F1",
"profile": "C:/Users/xxx/Desktop/result/Openharmony-signtest.p7b",
"signAlg": "SHA256withECDSA",
"storeFile": "C:/Users/xxx/Desktop/result/OpenHarmony-ABC.p12"
}
}
],点击编译,编译完成后自动hap自动安装至设备中。
定制签名配置导入源码
详细步骤可参考OpenHarmony应用签名 - 厂商私有签名的配置和使用参考文档中对于当前版本(3.2 Release)源码中签名配置不完善之处也给出了说明。本文这里以替换源码默认签名配置方式介绍导入定制签名配置的大致步骤,详细过程可以参见上述资料。
准备工作
#相关定制签名配置文件
hap签名工具包:hap-sign-tool.jar
定制签名密钥库:OpenHarmony-ABC.p12
定制签名密钥库密码:keystore123
Key alias密钥别名:OpenHarmony-ABC-subCA
密钥密码:subCA123
应用profile签名文件:OpenHarmony-ABC-app-cert.pem或OpenHarmony-ABC-app-cert.cer
profile签名模板:UnsgnedReleasedProfileTemplate.json
OpenHarmony 3.2 Release源码一份配置源码私有源签名信息
根据前文【验证定制签名】章节方式修改trusted_apps_sources.json和trusted_root_ca.json文件,替换源码默认私有源签名信息。base/security/appverify/interfaces/innerkits/appverify/config/OpenHarmony/trusted_apps_sources.json
{
"name":"OpenHarmony-ABC apps",
"app-signing-cert":"C=CN, O=OpenHarmony-ABC-app-cert, OU=OpenHarmony-ABC-app-cert Community, CN=OpenHarmony Application Release",
"profile-signing-certificate":"C=CN, O=OpenHarmony-ABC-profile-cert, OU=OpenHarmony-ABC-profile-cert Community, CN=OpenHarmony Application Profile Release",
"profile-debug-signing-certificate":"C=CN, O=OpenHarmony-ABC-profile-cert, OU=OpenHarmony-ABC-profile-cert Community, CN=OpenHarmony Application Profile Debug",
"issuer-ca":"C=CN, O=OpenHarmony-ABC-subCA, OU=OpenHarmony-ABC-subCA Community, CN=OpenHarmony Application CA",
"max-certs-path":3,
"critialcal-cert-extension":["keyusage"]
}base/security/appverify/interfaces/innerkits/appverify/config/OpenHarmony/trusted_root_ca.json
{
"C=CN, O=OpenHarmony-ABC-rootCA, OU=OpenHarmony-ABC-rootCA Community, CN=OpenHarmony Application Root CA":"-----BEGIN CERTIFICATE-----\nMIICQDCCAeagAwIBAgIFANIukcQwCgYIKoZIzj0EAwIwgYMxCzAJBgNVBAYTAkNO\nMR8wHQYDVQQKDBZPcGVuSGFybW9ueS1BQkMtcm9vdENBMSkwJwYDVQQLDCBPcGVu\nSGFybW9ueS1BQkMtcm9vdENBIENvbW11bml0eTEoMCYGA1UEAwwfT3Blbkhhcm1v\nbnkgQXBwbGljYXRpb24gUm9vdCBDQTAeFw0yMzA2MjgwMzE3NTlaFw0yNDA2Mjcw\nMzE3NTlaMIGDMQswCQYDVQQGEwJDTjEfMB0GA1UECgwWT3Blbkhhcm1vbnktQUJD\nLXJvb3RDQTEpMCcGA1UECwwgT3Blbkhhcm1vbnktQUJDLXJvb3RDQSBDb21tdW5p\ndHkxKDAmBgNVBAMMH09wZW5IYXJtb255IEFwcGxpY2F0aW9uIFJvb3QgQ0EwWTAT\nBgcqhkjOPQIBBggqhkjOPQMBBwNCAAQ/IK5FcvYOsKF8OpuiHRcR6zawSiPmVYp2\nAKahLN5CxjMTpVj14t23yG8RScJEOjuKUxh8SAqYr7lB0riOWJodo0UwQzAdBgNV\nHQ4EFgQUeb2WbI8s7xczwXlsuk8fo9eqmQUwEgYDVR0TAQH/BAgwBgEB/wIBADAO\nBgNVHQ8BAf8EBAMCAQYwCgYIKoZIzj0EAwIDSAAwRQIhANv5RhH5UtH0SXOh7k7+\nAVcBkn3Dqfdbu/LTShclS+APAiBpEe3s49fxpW7pNbGzdMEgaqXafuf5+YTT5VqF\n8PYydA==\n-----END CERTIFICATE-----\n"
}为了确保后续步骤的正确性,这里先进行简单的验证:编译源码,烧录images更新软件。安装使用定制签名的demo应用,若安装成功则说明上述json文件修改有效,否则需要检查上述json配置文件修改参数或demo应用定制签名配置。
替换源码默认编译签名配置
OpenHarmony-ABC.p12替换developtools\hapsigner\dist\OpenHarmony.p12OpenHarmony-ABC-app-cert.pem替换developtools\hapsigner\dist\OpenHarmonyApplication.pem注意:为了方便后续更新应用签名配置,仅更新上述两个签名配置内容,文件名不做更新,仍保留源码默认文件名OpenHarmony.p12和OpenHarmonyApplication.pem。
修改默认编译签名信息build/ohos_var.gni
default_hap_private_key_path = "OpenHarmony-ABC-subCA" //更新定制签名密钥别名
default_signature_algorithm = "SHA256withECDSA"
default_key_alias = "subCA123" //更新定制签名签名密钥密码
default_keystore_password = "keystore123" //更新定制签名密钥库密码
default_keystore_path = "//developtools/hapsigner/dist/OpenHarmony.p12"
default_hap_certificate_file =
"//developtools/hapsigner/dist/OpenHarmonyApplication.pem"更新系统应用及其定制签名配置文件
到这里源码BUILD.gn编译出的应用为使用定制签名配置签名应用。但源码中部分应用采用直接预置hap的方式,故需要另外使用定制签名配置生成hap后更新hap文件。需更新hap的应用:
输入法选择框:
base/inputmethod/imf/services/dialog/input_method_choose_dialog.hap
webview应用:
base\web\webview\ohos_nweb\prebuilts\arm64\NWeb.hap
系统默认部分预置应用:
applications\standard\hap\*.hap这里以更新BUILD.gn编译方式permissionmanager的应用和IDE编译的KikaInput输入法为例。
配置permissionmanager系统应用定制签名
applications\standard\permission_manager\signature\从permissionmanager原始pm.p7b中获取UnsgnedReleasedProfileTemplate.json信息
java -jar hap-sign-tool.jar verify-profile -inFile pm.p7b -outFile PM_UnsgnedReleasedProfileTemplate.json将PM_UnsgnedReleasedProfileTemplate.json的bundle-name、apl、app-feature、allowed-acls、permissions字段信息更新至用于重新生成pm.p7b的UnsgnedReleasedProfileTemplate.json。通过文本查看的方式打开pm.p7b将app-privilege-capabilities字段信息填入UnsgnedReleasedProfileTemplate.json。注意:UnsgnedReleasedProfileTemplate.json字段distribution-certificate需与上文第8小节distribution-certificate保持一致。详细见【8、将OpenHarmony-ABC-app-cert.pem中第一部分的密钥,把回车转换为\n字符,放入UnsgnedReleasedProfileTemplate.json的distribution-certificate中】。
生成新的pm.p7b
java -jar hap-sign-tool.jar sign-profile -mode "localSign" -keyAlias "OpenHarmony-ABC-profileCA" -keyPwd "profileCA123" -profileCertFile "./result/OpenHarmony-ABC-profile-cert-release.pem" -inFile "UnsgnedReleasedProfileTemplate.json" -signAlg "SHA256withECDSA" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -outFile "./result/pm.p7b"将pm.p7b和UnsgnedReleasedProfileTemplate.json一同更新至applications\standard\permission_manager\signature\接下来进行验证: 使用hb命令模块编译permissionmanager:
hb build -T applications/standard/permission_manager/permissionmanager:permission_manager
#得到签名hap
out\zp37a\obj\applications\standard\permission_manager\permissionmanager\permission_manager.hap更新vendor\hihope\rk3568\preinstall-config\install_list_capability.json或vendor\hihope\rk3568\preinstall-config\install_list_permissions.json中permisson_manager的app_signature,简单验证可修改后拷贝至设备/system/etc/app/。将out\zp37a\obj\applications\standard\permission_manager\permissionmanager\permission_manager.hap替换设备中的/system/app/com.ohos.permissionmanager/permission_manager.hap,删除data/分区后重启设备。重启后bm dump -a若查看到com.ohos.permissionmanager则说明签名后的permission_manager.hap已验签成功并重新安装。
配置KikaInput系统应用定制签名
同上方式,从applications\standard\app_samples\CompleteApps\KikaInput原始p7b中获取profile信息,并更新至UnsgnedReleasedProfileTemplate.json。使用UnsgnedReleasedProfileTemplate.json生成新的kikakeyboard.p7b
java -jar hap-sign-tool.jar sign-profile -mode "localSign" -keyAlias "OpenHarmony-ABC-profileCA" -keyPwd "profileCA123" -profileCertFile "./result/OpenHarmony-ABC-profile-cert-release.pem" -inFile "UnsgnedReleasedProfileTemplate.json" -signAlg "SHA256withECDSA" -keystoreFile "./result/OpenHarmony-ABC.p12" -keystorePwd "keystore123" -outFile "./result/kikakeyboard.p7b"将applications\standard\app_samples\CompleteApps\KikaInput导入IDE工程,并使用定制签名配置文件OpenHarmony.p12、kikakeyboard.p7b、OpenHarmony-ABC-app-cert.cer编译生成新的签名hap,替换设备/system/app/com.example.kikakeyboard/kikaInput.hap,更新vendor\hihope\rk3568\preinstall-config\install_list_capability.json或vendor\hihope\rk3568\preinstall-config\install_list_permissions.json中kikakeyboard的app_signature,修改后拷贝至设备/system/etc/app/。删除data分期后重启设备,重启后bm dump -a若查看到com.example.kikakeyboard则说明签名后的kikaInput.hap已验签成功并重新安装。
总结定制签名导入源码步骤:1、更新配置源码私有源签名信息文件trusted_apps_sources.json和trusted_root_ca.jsonbase/security/appverify/interfaces/innerkits/appverify/config/OpenHarmony/trusted_apps_sources.json base/security/appverify/interfaces/innerkits/appverify/config/OpenHarmony/trusted_root_ca.json 2、替换源码默认编译签名配置 developtools\hapsigner\dist\OpenHarmony.p12 developtools\hapsigner\dist\OpenHarmonyApplication.pem build/ohos_var.gni 3、更新预置应用p7b签名配置及hap 对于以预置hap方式的应用需收到生成定制签名的hap并将hap更新至源码中。 4、更新应用的app_signature签名指纹信息 vendor\hihope\rk3568\preinstall-config\install_list_capability.json vendor\hihope\rk3568\preinstall-config\install_list_permissions.json中 5、编译源码验证,bm dump -a查看各应用是否已安装上,各应用运行情况。
hap-sign-tool.jar帮助手册
$ java -jar hap-sign-tool.jar -h
06-27 19:28:02 INFO - /*
* Copyright (c) 2021-2022 Huawei Device Co., Ltd.
* Licensed under the Apache License, Version 2.0 (the "License");
* you may not use this file except in compliance with the License.
* You may obtain a copy of the License at
*
* http://www.apache.org/licenses/LICENSE-2.0
*
* Unless required by applicable law or agreed to in writing, software
* distributed under the License is distributed on an "AS IS" BASIS,
* WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
* See the License for the specific language governing permissions and
* limitations under the License.
*/
USAGE: <generate-keypair|generate-csr|generate-cert|generate-ca|generate-app-cert|generate-profile-cert> [options]
USAGE: <sign-profile|verify-profile|sign-app|verify-app> [options]
generate-keypair [options]:
-keyAlias : key alias, required fields;
-keyPwd : key password, optional fields;
-keyAlg : key algorithm, required fields, including RSA/ECC;
-keySize : key size, required fields, the size of the RSA algorithm is 2048/3072/4096, and the size of the ECC algorithm is NIST-P-256/NIST-P-384;
-keystoreFile : keystore file, required fields, JKS or P12 format;
-keystorePwd : keystore password, optional fields;
-extCfgFile : Extend Profile, optional fields;
EXAMPLE:
generate-keypair -keyAlias "oh-app1-key-v1" -keyPwd ****** -keyAlg ECC -keySize NIST-P-256 -keystoreFile "D:\OH\app-keypair.jks" -keystorePwd ******
generate-keypair -keyAlias "oh-profile-key-v1" -keyPwd ****** -keyAlg RSA -keySize 2048 -keystoreFile "D:\OH\profile-keypair.jks" -keystorePwd ******
generate-csr [options]:
-keyAlias : key alias, required fields;
-keyPwd : key password, optional fields;
-subject : certificate subject, required fields;
-signAlg : signature algorithm, required fields, including SHA256withRSA/SHA384withRSA/SHA256withECDSA/SHA384withECDSA;
-keystoreFile : keystore file, required fields, JKS or P12 format;
-keystorePwd : keystore password, optional fields;
-outFile : output file, optional fields, if not filled, it will be directly output to the console;
-extCfgFile : Extend Profile, optional fields;
EXAMPLE:
generate-csr -keyAlias "oh-app1-key-v1" -keyPwd ****** -subject "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=App1 Release" -signAlg SHA256withECDSA -keystoreFile "D:\OH\app-keypair.jks" -keystorePwd ****** -outFile "D:\OH\oh-app1-key-v1.csr"
generate-cert [options]:
-keyAlias : key alias, required fields;
-keyPwd : key password, optional fields;
-issuer : issuer subject, required fields;
-issuerKeyAlias : issuer key alias, required fields;
-issuerKeyPwd : issuer key password, optional fields;
-subject : certificate subject, required fields;
-validity : certificate validity, optional fields, the default is 1095 days;
-keyUsage : key usage, required fields, including digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment, keyAgreement, certificateSignature, crlSignature, encipherOnly and decipherOnly, if the certificate includes multiple key usages, separate them with commas;
-keyUsageCritical : whether keyUsage is a key item, optional fields, the default is true;
-extKeyUsage : extended key usage, optional fields, including clientAuthentication, serverAuthentication, codeSignature, emailProtection, smartCardLogin, timestamp, ocspSignature;
-extKeyUsageCritical : whether extKeyUsage is a key item, optional fields, the default is false;
-signAlg : signature algorithm, required fields, including SHA256withRSA/SHA384withRSA/SHA256withECDSA/SHA384withECDSA;
-basicConstraints : whether to include basicConstraints, optional fields, the default is false;
-basicConstraintsCritical : whether basicConstraints is a key item, optional fields, the default is false;
-basicConstraintsCa : whether it is CA, optional fields, the default is false;
-basicConstraintsPathLen : basicConstraints path length, optional fields, the default is 0;
-keystoreFile : keystore file, required fields, JKS or P12 format;
-keystorePwd : keystore password, optional fields;
-outFile : output file, optional fields, if not filled, it will be directly output to the console;
-extCfgFile : Extend Profile, optional fields;
-issuerKeystoreFile : issuer keystore file, optional fields, JKS or P12 format;
-issuerKeystorePwd : issuer keystore password, optional fields;
EXAMPLE:
generate-cert -keyAlias "oh-app1-key-v1" -keyPwd ****** -issuer "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Application Signature Service CA" -issuerKeyAlias "oh-app-sign-srv-ca-key-v1" -issuerKeyPwd ****** -subject "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=App1 Release" -validity 365 -keyUsage digitalSignature -extKeyUsage codeSignature -signAlg SHA256withECDSA -keystoreFile "D:\OH\app-keypair.jks" -keystorePwd ****** -outFile "D:\OH\app1.cer"
generate-ca [options]:
-keyAlias : key alias, required fields;
-keyPwd : key password, optional fields;
-keyAlg : key algorithm, required fields, including RSA/ECC;
-keySize : key size, required fields, the size of the RSA algorithm is 2048/3072/4096, and the size of the ECC algorithm is NIST-P-256/NIST-P-384;
-issuer : issuer subject, optional fields, if it is empty, it means root CA;
-issuerKeyAlias : issuer key alias, optional fields, if it is empty, it means root CA;
-issuerKeyPwd : issuer key password, optional fields;
-subject : certificate subject, required fields;
-validity : certificate validity, optional fields, the default is 3650 days;
-signAlg : signature algorithm, required fields, including SHA256withRSA/SHA384withRSA/SHA256withECDSA/SHA384withECDSA;
-basicConstraintsPathLen : basicConstraints path length, optional fields, the default is 0;
-keystoreFile : keystore file, required fields, JKS or P12 format;
-keystorePwd : keystore password, optional fields;
-outFile : output file, optional fields, if not filled, it will be directly output to the console;
-extCfgFile : Extend Profile, optional fields;
-issuerKeystoreFile : issuer keystore file, optional fields, JKS or P12 format;
-issuerKeystorePwd : issuer keystore password, optional fields;
EXAMPLE:
generate-ca -keyAlias "oh-root-ca-key-v1" -subject "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Root CA" -validity 365 -signAlg SHA384withECDSA -keystoreFile "D:\OH\app-keypair.jks" -keystorePwd ****** -outFile "D:\OH\root-ca.cer" -keyAlg RSA -keySize 2048
generate-ca -keyAlias "oh-app1-key-v1" -keyAlg RSA -keySize 2048 -issuer "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Root CA" -issuerKeyAlias "oh-sub-app-ca-key-v1" -issuerKeyPwd ****** -subject "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN= Application Signature Service CA" -validity 365 -signAlg SHA384withECDSA -keystoreFile "D:\OH\app-keypair.jks" -keystorePwd ****** -outFile "D:\OH\sub-app-sign-srv-ca.cer"
generate-ca -keyAlias "oh-profile-key-v1" -keyAlg RSA -keySize 4096 -issuer "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Root CA" -issuerKeyAlias "oh-sub-profile-ca-key-v1" -issuerKeyPwd ****** -subject "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN= Profile Signature Service CA" -validity 365 -signAlg SHA384withECDSA -keystoreFile "D:\OH\profile-keypair.jks" -keystorePwd ****** -outFile "D:\OH\sub-profile-sign-srv-ca.cer"
generate-app-cert [options]:
-keyAlias : key alias, required fields;
-keyPwd : key password, optional fields;
-issuer : issuer subject, required fields;
-issuerKeyAlias : issuer key alias, required fields;
-issuerKeyPwd : issuer key password, optional fields;
-subject : certificate subject, required fields;
-validity : certificate validity, optional fields, the default is 1095 days;
-signAlg : signature algorithm, required fields, including SHA256withRSA/SHA384withRSA/SHA256withECDSA/SHA384withECDSA;
-keystoreFile : keystore file, required fields, JKS or P12 format;
-keystorePwd : keystore password, optional fields;
-outForm : the format of the output certificate file, including cert/certChain, optional fields, the default is cert;
-rootCaCertFile : root CA certificate file, required when outForm is certChain;
-subCaCertFile : secondary sub-CA certificate file, required when outForm is certChain;
-outFile : output certificate file (certificate or certificate chain), optional fields, if not filled, it will be directly output to the console;
-extCfgFile : Extend Profile, optional fields;
-issuerKeystoreFile : issuer keystore file, optional fields, JKS or P12 format;
-issuerKeystorePwd : issuer keystore password, optional fields;
EXAMPLE:
generate-app-cert -keyAlias "oh-app1-key-v1" -keyPwd ****** -issuer "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Application Debug Signature Service CA" -issuerKeyAlias "oh-app-sign-debug-srv-ca-key-v1" -subject "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=App1 Debug" -validity 365 -signAlg SHA256withECDSA -rootCaCertFile "D:\OH\root-ca.cer" -subCaCertFile "D:\OH\sub-app-sign-srv-ca.cer" -keystoreFile "D:\OH\app-keypair.jks" -keystorePwd ****** -outForm certChain -outFile "D:\OH\app-debug-cert.cer"
generate-app-cert -keyAlias "oh-app1-key-v1" -keyPwd ****** -issuer "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Application Release Signature Service CA" -issuerKeyAlias "oh-app-sign-release-srv-ca-key-v1" -subject "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=App1 Release" -validity 365 -signAlg SHA256withECDSA -rootCaCertFile "D:\OH\root-ca.cer" -subCaCertFile "D:\OH\sub-app-sign-srv-ca.cer" -keystoreFile "D:\OH\app-keypair.jks" -keystorePwd ****** -outForm certChain -outFile "D:\OH\app-release-cert.cer"
generate-profile-cert [options]:
-keyAlias : key alias, required fields;
-keyPwd : key password, optional fields;
-issuer : issuer subject, required fields;
-issuerKeyAlias : issuer key alias, required fields;
-issuerKeyPwd : issuer key password, optional fields;
-subject : certificate subject, required fields;
-validity : certificate validity, optional fields, the default is 1095 days;
-signAlg : signature algorithm, required fields, including SHA256withRSA/SHA384withRSA/SHA256withECDSA/SHA384withECDSA;
-keystoreFile : keystore file, required fields, JKS or P12 format;
-keystorePwd : keystore password, optional fields;
-outForm : the format of the output certificate file, including cert/certChain, optional fields, the default is cert;
-rootCaCertFile : root CA certificate file, required when outForm is certChain;
-subCaCertFile : secondary sub-CA certificate file, required when outForm is certChain;
-outFile : output file, optional fields, if not filled, it will be directly output to the console;
-extCfgFile : Extend Profile, optional fields;
-issuerKeystoreFile : issuer keystore file, optional fields, JKS or P12 format;
-issuerKeystorePwd : issuer keystore password, optional fields;
EXAMPLE:
generate-profile-cert -keyAlias "oh-profile-key-v1" -keyPwd ****** -issuer "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Provision Profile Debug Signature Service CA" -issuerKeyAlias "oh-profile-sign-debug-srv-ca-key-v1" -issuerKeyPwd ****** -subject "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Provision Profile Debug" -validity 365 -signAlg SHA256withECDSA -rootCaCertFile "D:\OH\root-ca.cer" -subCaCertFile "D:\OH\sub-profile-sign-srv-ca.cer" -keystoreFile "D:\OH\profile-keypair.jks" -keystorePwd ****** -outForm certChain -outFile "D:\OH\provision-profile-debug.cer"
generate-profile-cert -keyAlias "oh-profile-key-v1" -keyPwd ****** -issuer "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Provision Profile Release Signature Service CA" -issuerKeyAlias "oh-profile-sign-release-srv-ca-key-v1" -issuerKeyPwd ****** -subject "C=CN,O=OpenHarmony,OU=OpenHarmony Community,CN=Provision Profile Release" -validity 365 -signAlg SHA256withECDSA -rootCaCertFile "D:\OH\root-ca.cer" -subCaCertFile "D:\OH\sub-profile-sign-srv-ca.cer" -keystoreFile "D:\OH\profile-keypair.jks" -keystorePwd ****** -outForm certChain -outFile "D:\OH\provision-profile-release.cer"
sign-profile [options]:
-mode : signature mode, required fields, including localSign/remoteSign;
-keyAlias : key alias, required fields;
-keyPwd : key password, optional fields;
-profileCertFile : profile signing certificate (certificate chain, the order is three-level-two-root), required fields;
-inFile : input original Provision Profile file, required fields;
-signAlg : signature algorithm, required fields, including SHA256withRSA/SHA384withRSA/SHA256withECDSA/SHA384withECDSA;
-keystoreFile : keystore file, if signature mode is localSign, required fields, JKS or P12 format;
-keystorePwd : keystore password, optional fields;
-outFile : output the signed Provision Profile file, p7b format, required fields;
-extCfgFile : Extend Profile, optional fields;
EXAMPLE:
sign-profile -mode localSign -keyAlias "oh-profile-key-v1" -keyPwd ****** -profileCertFile "D:\OH\provision-profile-release.cer" -inFile "D:\OH\app1-profile-release.json" -signAlg SHA256withECDSA -keystoreFile "D:\OH\profile-keypair.jks" -keystorePwd ****** -outFile "D:\OH\signed-profile.p7b"
verify-profile [options]:
-inFile : signed Provision Profile file, p7b format, required fields;
-outFile : Verification result file (including verification result and profile content), json format, optional; if not filled, it will be directly output to the console;
-extCfgFile : Extend Profile, optional fields;
EXAMPLE:
verify-profile -inFile "D:\OH\signed-profile.p7b" -outFile "D:\OH\VerifyResult.json"
sign-app [options]:
-mode : signature mode, required fields, including localSign/remoteSign/remoteResign;
-keyAlias : key alias, required fields;
-keyPwd : key password, optional fields on localSign mode;
-appCertFile : application signature certificate file, required fields on localSign mode, optional fields on remoteSign mode;
-profileFile : signed Provision Profile file, p7b format, required fields;
-profileSigned : indicates whether the profile file has a signature.The options are as follows: 1:yes; 0:no; default value:1. optional fields;
-inFile : input original application package file, hap or bin format, required fields;
-signAlg : signature algorithm, required fields, including SHA256withRSA/SHA384withRSA/SHA256withECDSA/SHA384withECDSA;
-keystoreFile : keystore file, if signature mode is localSign, required fields on localSign mode, JKS or P12 format;
-keystorePwd : keystore password, optional fields on localSign mode;
-outFile : output the signed Provision Profile file, required fields;
-extCfgFile : Extend Profile, optional fields;
-inForm : enter the format of the original file, the format is .zip or .bin;
-compatibleVersion : min compatible api version for running app, required fields while input original application package file format is hap;
-signServer : remote signer plugin, required fields on remoteSign mode;
-signerPlugin : remote sign service url, required fields on remoteSign mode;
-onlineAuthMode : remote sign auth mode, required fields on remoteSign mode, including account;
-username : user account for online auth, required fields on remoteSign mode with account auth mode;
-userPwd : user password for online auth, required fields on remoteSign mode with account auth mode;
-ext : extend parameters for remote signer plugin, optional fields;
EXAMPLE:
sign-app -mode localSign -keyAlias "oh-app1-key-v1" -appCertFile "D:\OH\app-release-cert.cer" -profileFile "D:\OH\signed-profile.p7b" -inFile "D:\OH\app1-unsigned.hap" -signAlg SHA256withECDSA -keystoreFile "D:\OH\app-keypair.jks" -keystorePwd ****** -outFile "D:\OH\app1-signed.hap -compatibleVersion 8"
verify-app [options]:
-inFile : signed application package file, hap or bin format, required fields;
-outCertChain : signed certificate chain file, required fields;
-outProfile : profile file in application package, required fields;
-extCfgFile : Extend Profile, optional fields;
EXAMPLE:
verify-app -inFile "D:\OH\app1-signed.hap" -outCertChain "outCertChain.cer" -outProfile "outprofile.p7b"
COMMANDS:
generate-keypair : generate key pair
generate-csr : generate certificate signing request
generate-cert : generate certificate in full, large and complete, any certificate can be generated
generate-ca : generate root/subject CA certificate, if the key does not exist, generate the key together
generate-app-cert : generate application debug/release certificate
generate-profile-cert : generate application debug/release certificate
sign-profile : Provision Profile file signature
verify-profile : Provision Profile file verification
sign-app : application package signature
verify-app : application package file verification| 阿里云国内75折 回扣 微信号:monov8 |
| 阿里云国际,腾讯云国际,低至75折。AWS 93折 免费开户实名账号 代冲值 优惠多多 微信号:monov8 飞机:@monov6 |

