capture the ether靶场题解(Account)
| 阿里云国内75折 回扣 微信号:monov8 |
| 阿里云国际,腾讯云国际,低至75折。AWS 93折 免费开户实名账号 代冲值 优惠多多 微信号:monov8 飞机:@monov6 |
题目预览
Fuzzy identity
分析
题目合约
pragma solidity ^0.4.21;
interface IName {
function name() external view returns (bytes32);
}
contract FuzzyIdentityChallenge {
bool public isComplete;
function authenticate() public {
require(isSmarx(msg.sender));
require(isBadCode(msg.sender));
isComplete = true;
}
function isSmarx(address addr) internal view returns (bool) {
return IName(addr).name() == bytes32("smarx");
}
function isBadCode(address _addr) internal pure returns (bool) {
bytes20 addr = bytes20(_addr);
bytes20 id = hex"000000000000000000000000000000000badc0de";
bytes20 mask = hex"000000000000000000000000000000000fffffff";
for (uint256 i = 0; i < 34; i++) {
if (addr & mask == id) {
return true;
}
mask <<= 4;
id <<= 4;
}
return false;
}
}
题目要求我们将isComplete变为true。
很明显必须调用authenticate函数也就要饶过两个require。
第一个require要求我们满足IName函数并且返回值为bytes32(“smarx”)很容易满足。
第二个require意思是我们用来攻击的地址中必须存在"badc0de"这一串字符也就很容易想到使用creat2来完成。
攻击
攻击合约
pragma solidity ^0.4.21;
import "./FuzzyIdentity.sol";
contract attack{
function name() external view returns (bytes32){
return bytes32("smarx");
}
function att(address _Fuzzy) public {
FuzzyIdentityChallenge(_Fuzzy).authenticate();
}
}
部署合约
contract deployer{
bytes attackCode = hex"608060405234801561001057600080fd5b5061019a806100206000396000f30060806040526004361061004c576000357c0100000000000000000000000000000000000000000000000000000000900463ffffffff16806306fdde0314610051578063db97040214610084575b600080fd5b34801561005d57600080fd5b506100666100c7565b60405180826000191660001916815260200191505060405180910390f35b34801561009057600080fd5b506100c5600480360381019080803573ffffffffffffffffffffffffffffffffffffffff1690602001909291905050506100ef565b005b60007f736d617278000000000000000000000000000000000000000000000000000000905090565b8073ffffffffffffffffffffffffffffffffffffffff1663380c7a676040518163ffffffff167c0100000000000000000000000000000000000000000000000000000000028152600401600060405180830381600087803b15801561015357600080fd5b505af1158015610167573d6000803e3d6000fd5b50505050505600a165627a7a723058204273cdd8b92be0f5d505d2cc5fb213a3d50227101e51e54b95e9bd5592b6c6e80029";
function deploy(bytes32 salt) public returns(address){
bytes memory bytecode = attackCode;
address addr;
assembly {
addr := create2(0, add(bytecode, 0x20), mload(bytecode), salt)
}
return addr;
}
function getHash()public view returns(bytes32){
return keccak256(attackCode);
}
}
思路很简单使用creat2我们知道creat2可以根据用户输入salt的不同部署可控地址的合约我们只需要将攻击合约的字节码放入deploy函数再根据脚本算出生成对应地址需要的salt。
脚本如下
from web3 import Web3
s1 = '0xff7EF2e0048f5bAeDe046f6BF797943daF4ED8CB47'
s3 = '35206f900ec99a80b49aaffd98e9ad7e94f0de8df30a79b6797d52f7eaa76ea1'
i = 0
while(1):
salt = hex(i)[2:].rjust(64, '0')
s = s1+salt+s3
hashed = Web3.sha3(hexstr=s)
hashed_str = ''.join(['%02x' % b for b in hashed])
if 'badc0de' in hashed_str[24:]:
print(salt,hashed_str)
break
i += 1
print(salt)
将部署合约的地址放入s1攻击合约字节码哈希后放入s3经过一段时间即可生成出salt将salt放入deploy函数即成功部署attack合约调用攻击函数即可。
Public Key
分析
题目合约
pragma solidity ^0.4.21;
contract PublicKeyChallenge {
address owner = 0x92b28647ae1f3264661f72fb2eb9625a89d88a31;
bool public isComplete;
function authenticate(bytes publicKey) public {
require(address(keccak256(publicKey)) == owner);
isComplete = true;
}
}
合约要求我们输入的参数哈希后为owner的地址简单来说就是要我们拿到这个地址的公钥。
这里涉及到以太坊上公私钥生成算法和椭圆曲线数字签名算法这里不细讲只需要知道当知道消息hashr,s,v也就是消息签名 的三部分我们就可以得到对应的公钥。
我们去区块链浏览器上查询该地址曾经的交易记录很轻松能够查到这笔由该地址发出的交易
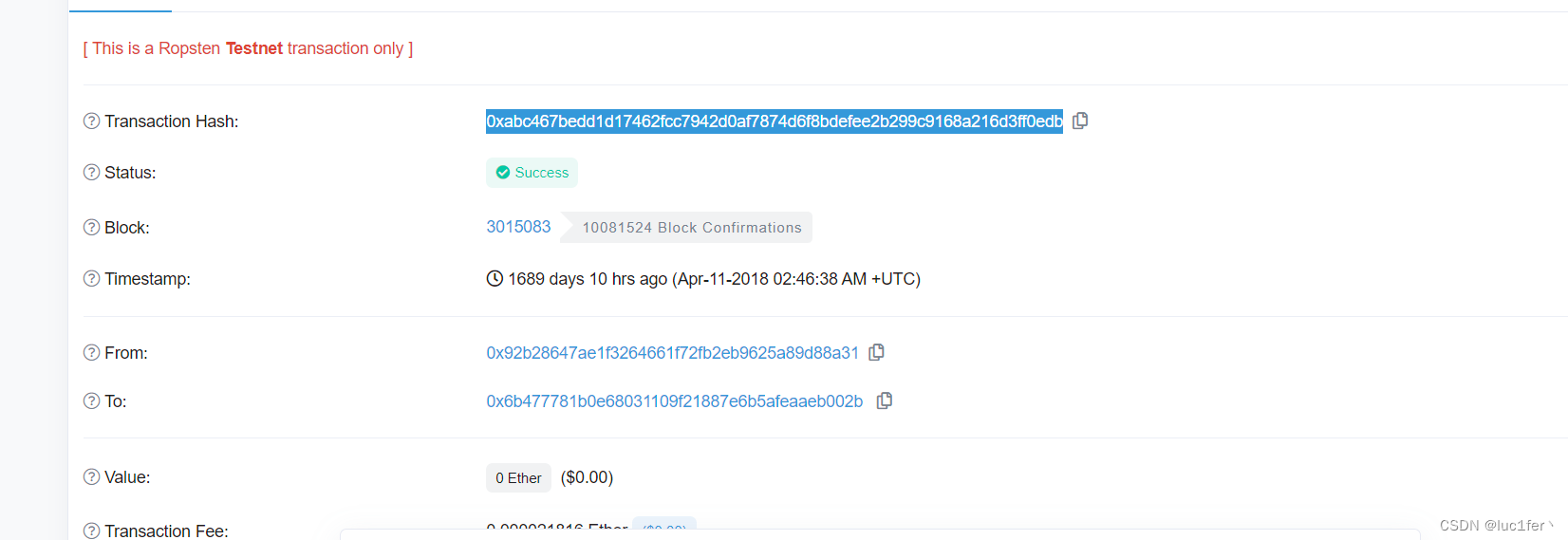
根据web3.eth.getTransaction来获取到该交易的hash,r,s,v
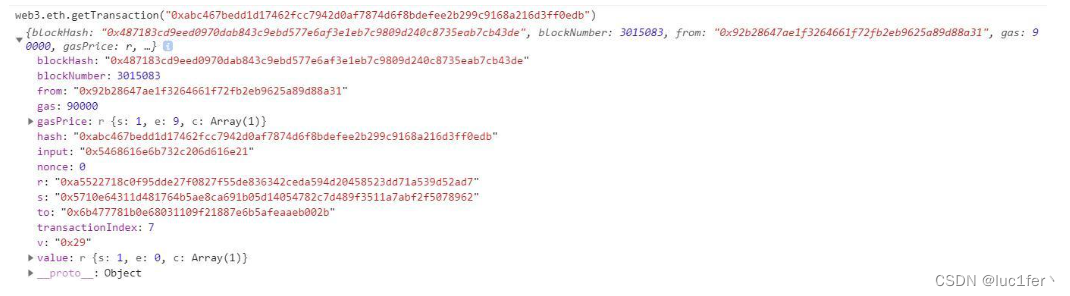
利用这些已知数据通过脚本来获取到对应的公钥脚本如下
const EthereumTx = require('ethereumjs-tx');
const util = require('ethereumjs-util');
var rawTx = {
nonce: '0x00',
gasPrice: '0x3b9aca00',
gasLimit: '0x15f90',
to: '0x6B477781b0e68031109f21887e6B5afEAaEB002b',
value: '0x00',
data: '0x5468616e6b732c206d616e21',
v: '0x29',
r: '0xa5522718c0f95dde27f0827f55de836342ceda594d20458523dd71a539d52ad7',
s: '0x5710e64311d481764b5ae8ca691b05d14054782c7d489f3511a7abf2f5078962'
};
var tx = new EthereumTx(rawTx);
pubkey=tx.getSenderPublicKey();
pubkeys=pubkey.toString('hex');
var address = util.sha3(pubkey).toString('hex').slice(24);
console.log(pubkeys);
console.log(address);
将对应的公钥放入authenticate调用即可。
攻击
运行脚本算出公钥
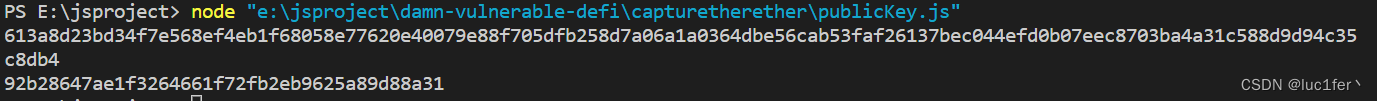
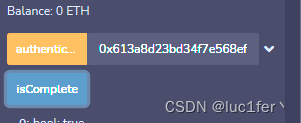
公钥放入函数调用栏调用即可完成
Account Takeover
分析
题目合约
pragma solidity ^0.4.21;
contract AccountTakeoverChallenge {
address owner = 0x6B477781b0e68031109f21887e6B5afEAaEB002b;
bool public isComplete;
function authenticate() public {
require(msg.sender == owner);
isComplete = true;
}
}
与上题有些类似只不过这个题需要我们拿到账户的私钥并根据私钥使用该账户来调用这个函数。
同样能够在区块链浏览器上查到交易且我们能够发现本来r应该唯一的交易确存在两笔交易拥有相同的r我们可以根据这个计算出对应账户的私钥。
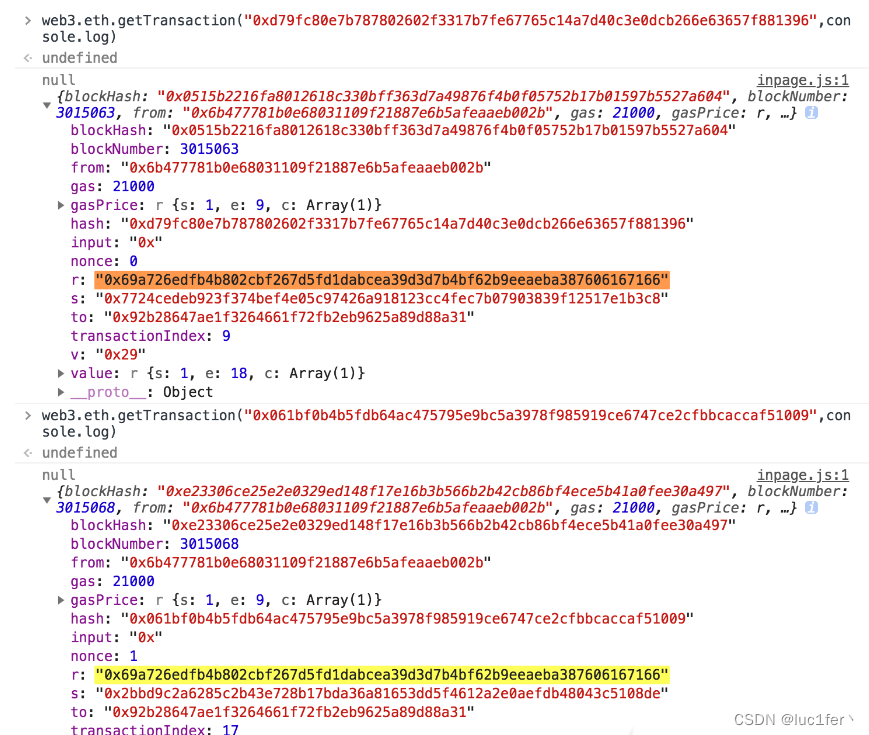
攻击
攻击脚本
# -*-coding:utf-8-*-
from web3 import Web3, HTTPProvider
from pwn import log
infura_url = 'https://ropsten.infura.io/v3/[api_key]'
web3 = Web3(Web3.HTTPProvider(infura_url))
a= web3.eth.get_transaction("0x061bf0b4b5fdb64ac475795e9bc5a3978f985919ce6747ce2cfbbcaccaf51009")
log.info("r = {0}".format(a.r.hex()))
log.info("s = {0}".format(a.s.hex()))
log.info("v= {0}".format(a.v))
a= web3.eth.get_transaction("0xd79fc80e7b787802602f3317b7fe67765c14a7d40c3e0dcb266e63657f881396")
log.info("r = {0}".format(a.r.hex()))
log.info("s = {0}".format(a.s.hex()))
log.info("v= {0}".format(a.v))
r = 0x69a726edfb4b802cbf267d5fd1dabcea39d3d7b4bf62b9eeaeba387606167166
# txid:
0xd79fc80e7b787802602f3317b7fe67765c14a7d40c3e0dcb266e63657f881396
s2 = 0x7724cedeb923f374bef4e05c97426a918123cc4fec7b07903839f12517e1b3c8
z2 = 0x350f3ee8007d817fbd7349c477507f923c4682b3e69bd1df5fbb93b39beb1e04
# txid:
0x061bf0b4b5fdb64ac475795e9bc5a3978f985919ce6747ce2cfbbcaccaf51009
s1 = 0x2bbd9c2a6285c2b43e728b17bda36a81653dd5f4612a2e0aefdb48043c5108de
z1 = 0x4f6a8370a435a27724bbc163419042d71b6dcbeb61c060cc6816cda93f57860c
# prime order p
p = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
# based on Fermat's Little Theorem
# works only on prime n
def inverse_mod(a, n):
return pow(a, n - 2, n)
k=(z1-z2)*inverse_mod(s1-s2,p)%p #derivekfors1-s2
pk = (s1 * k - z1) * inverse_mod(r, p) % p # derive private key
pkNeg=(-s1*(-k%p)-z1)*inverse_mod(r,p)%p #-k(modp)of s1 - s2 == -s1 + s2, check -s1
log.info('k = {:x}'.format(k))
log.info('k negation = {:x}'.format(-k % p))
if pk == pkNeg: # should not be false
log.success('private key = {:x}'.format(pk))
k=(z1-z2)*inverse_mod(s1+s2,p)%p #derivekfors1+s2
pk = (s1 * k - z1) * inverse_mod(r, p) % p # derive private key pkNeg=(-s1*(-k%p)-z1)*inverse_mod(r,p)%p #-k(modp)of s1 + s2 == -s1 - s2, double check -s1
log.info('k = {:x}'.format(k))
log.info('k negation = {:x}'.format(-k % p))
if pk == pkNeg: # should not be false
log.success('private key = {:x}'.format(pk))
from eth_account import Account
acct =Account.from_key("614f5e36cd55ddab0947d1723693fef5456e5bee24738ba90bd33c0c6e68e269")
log.info('account addr {:x}'.format(acct.address))
私钥计算出来后导入账户并使用该账户调用合约即可。

